PATENTS
VARIOUS METHODS AND APPARATUSES FOR PORTABLE APPLICATIONS

Embodiments described herein relate to systems and methods for providing dynamic insertion of in-scene and non-in-scene secondary content. Secondary content insertion markers are encoded within the primary content, indicating that a particular type of secondary content (e.g., in-scene or non-in-scene) may be inserted at a time associated with the marker. When the insertion is in-scene, a portion of the primary content between two in-scene secondary content insertion markers may be replaced with alternative content that includes the portion of the primary content, supplemented with inserted secondary content
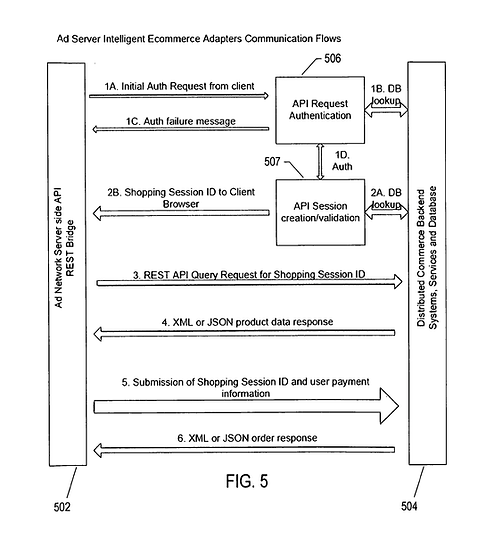
Certain embodiments of the present invention are directed to a real-time system that integrates data between an advertising system and an ecommerce system. The real-time system includes a distributed commerce platform that receives ecommerce data from the ecommerce system, delivers an ecommerce application to the ecommerce system, and that receives requests from a third party advertisement delivery platform.

A method, apparatus, and system for securing internet applications including a first internet application hosted on a source server and stored on a physical storage medium of the source server. The internet application is served across a network onto a client machine and contains code scripted to temporarily install on the client machine. The internet application shell container contains code scripted for a user interface to solicit sensitive data from a user of the client machine and a dual encryption security system including. A security communication manager employs an encrypted protocol where the identity of both a sender and a receiver of the transmitted data are both authenticated and the authentication between the client and source server is bilateral. Additionally, the security communication manager transmits the solicited sensitive data from the user interface by cooperating with the encryption engine. The systems and methods can identity theft and fraudulent activity.